Search results for tag #dns
The standalone Proxmox server is basically done at this point, all three DNS servers are online and secure, the Tailscale VM is online after completely forgetting that it was running on one of the Raspberry Pis, and the `authentik` instance that I'm gonna need to work on tomorrow.
The world decided not to call multistakeholer internet governance mean names: https://news.un.org/en/story/2025/12/1166623
As someone who had to think about how transitioning internet root management would work, I always wonder how the scary UN takeover would be accomplished. That's been postponed. Yay! hopefully there'll be less arguments about governance, allowing airtime for other important arguments about AI and global junkets. also yay!
Here is auDA's writeup https://www.auda.org.au/news-insights/blog/celebrating-a-success-at-wsis-20/
AWS Lambda functions changed the link local address for the internal resolver. for reasons.
caused some of my CDS monitoring functions to fail. I've fixed it now and am in the process of adding some resilience. #dns #dnssec
https://kalfeher.com/analysis/cds-charts/
RE: https://hachyderm.io/@dotmeow/115747548039870274
I’m planning to back this. Just have to negotiate with the family CFO on how much. I wants some meows!
#dns #domains
RE: https://infosec.exchange/@pft/115739987509166323
Less than half an hour: make sure to show the world that you know how to operate #DNS.
I need to transfer zone data, should I use the technique from 1987 or the new and improved one from 1996?
👩💼👨💼 LinkedIn Link Leading to Looted Login? 🧟🔐 [2/2]
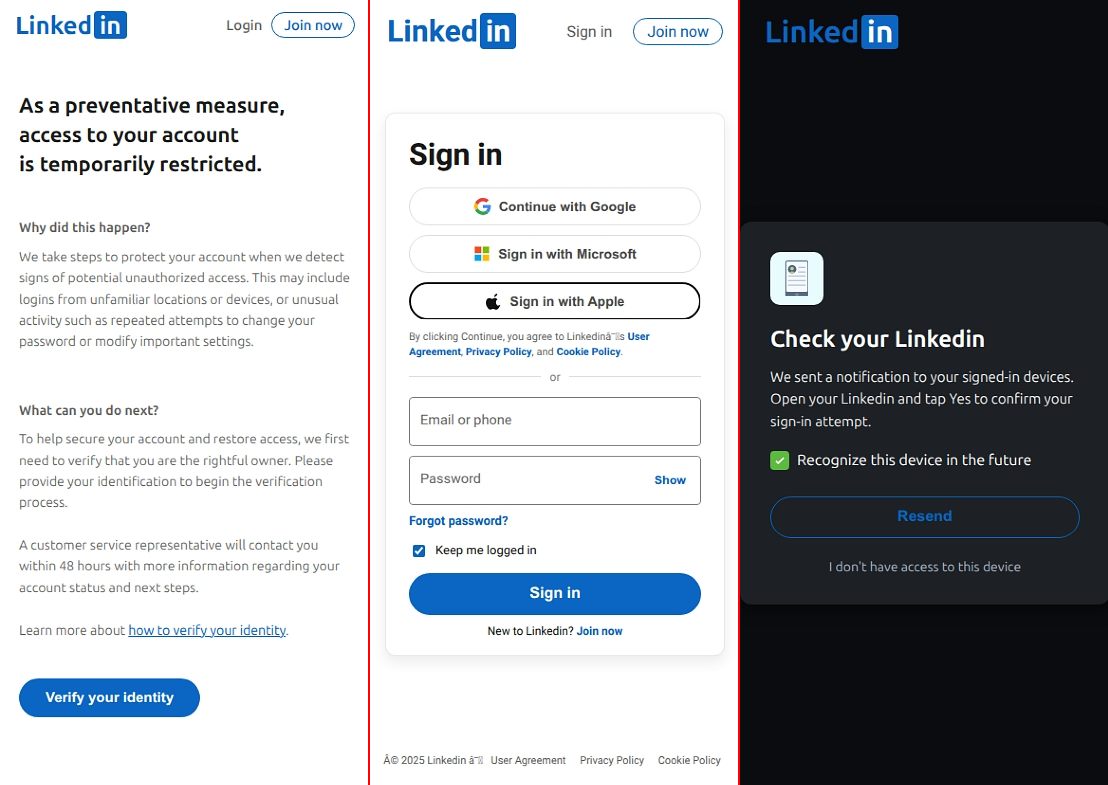
The site continues the ruse that the account is "temporarily restricted" and asks to "Verify your identity":
🐟 Mimics a login page and prompts for LinkedIn credentials (the Google, Microsoft, and Apple sign-in buttons seemingly do nothing)
🐟 Entered credentials are sent to the threat actor via a Google Apps Script, along with the victim's IP address and geolocation
🐟 Potential MFA bypass attempts:
🙀 Asks for confirmation of the sign-in attempt within the LinkedIn app
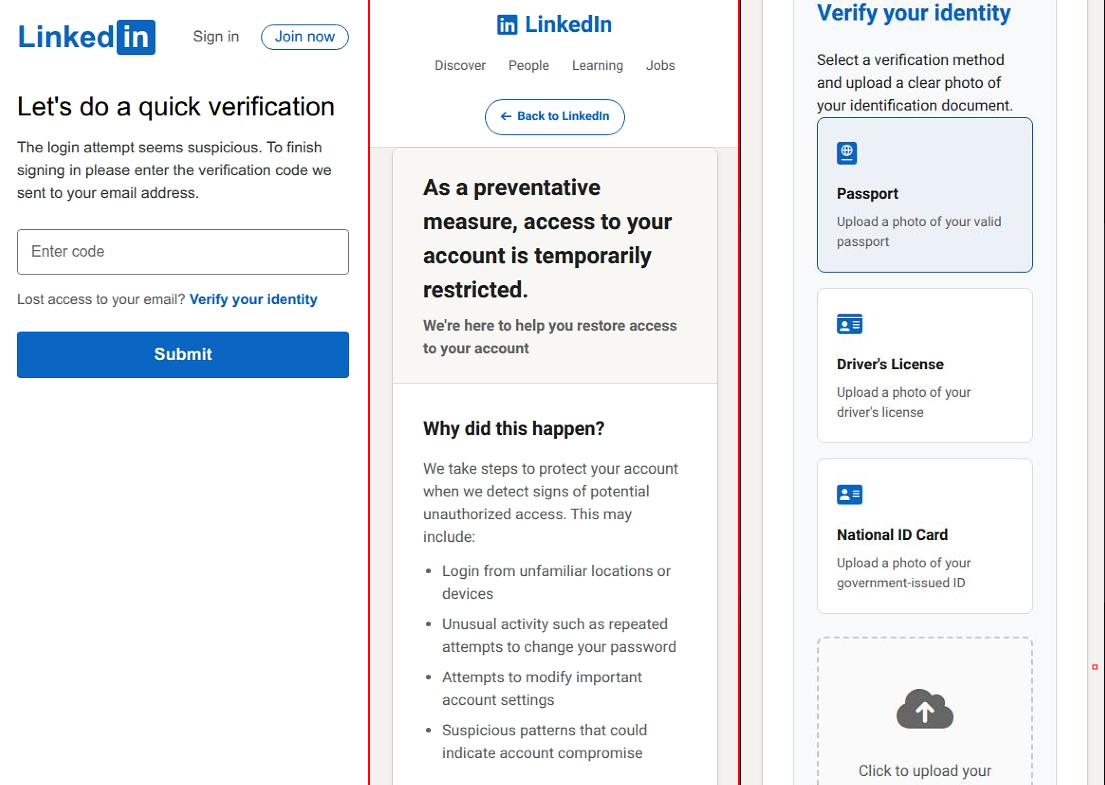
🙀 Warns that the 'login attempt seems suspicious' and asks for the 'verification code sent via email' to be entered
At this point an "Appeal submitted" page is typically displayed, although on one occasion we were prompted to upload a snap of our passport, driver's license or national ID card as access to our account was "temporarily restricted".
Regardless of the outcome, both 'success' pages suggest that someone posing as LinkedIn might make contact, perhaps a hint of further social engineering!
#dns #threatintel #threatintelligence #cybercrime #cybersecurity #infosec #infoblox #infobloxthreatintel #phishing
👩💼👨💼 LinkedIn Link Leading to Looted Login? 🧟🔐 [1/2]
LinkedIn users should watch out for fake 'policy violation' messages, especially if you're the sharing type!
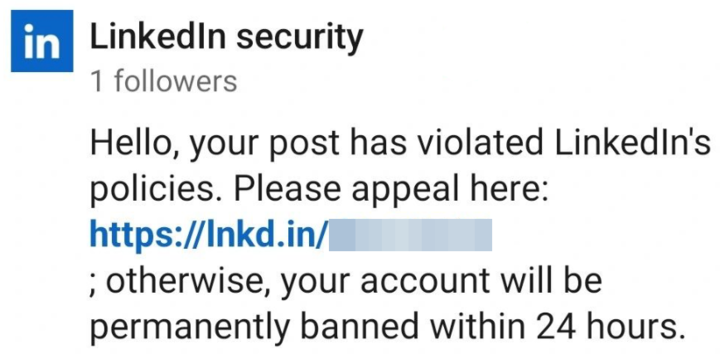
Over the past week, we've seen a threat actor masquerading as LinkedIn Security and posting replies to various posts:
"Hello, your post has violated LinkedIn's policies. Please appeal here: https://lnkd[.]in/<SHORT_URL>;
otherwise, your account will be permanently banned within 24 hours."
Given the legitimate LinkedIn short URL and the abuse of LinkedIn's branding in the attacker profile, some may be tempted to click and find themselves redirected to a phishing domain.
These domains are currently using the naming convention 'linkedverifycase' followed by some random numbers, for example:
🚨 linkedverifycase1289[.]com
🚨 linkedverifycase12168[.]com
🚨 linkedverifycase859369[.]com
#dns #threatintel #threatintelligence #cybercrime #cybersecurity #infosec #infoblox #infobloxthreatintel #phishing
Think parked domains are no big deal? Think again! These domains might seem benign on the surface, but our investigation into the risks of visiting parked domains might surprise you. In fact, if you were to visit a parked domain and actually see that typical park page, consider yourself lucky. Today, visits to these parked domains, which often happen accidentally, have become a source for traffic distribution systems, using a technique referred to by some as direct or zeroclick searches. In our experience this technique is much more likely to send you to threats like scams and malware. ClickFix? Sure. Results resembling what you were actually seeking? Not likely. To see what we found, check out our blog: https://blogs.infoblox.com/threat-intelligence/parked-domains-become-weapons-with-direct-search-advertising/
#InfobloxThreatIntel #dns #threatintel #threatintelligence #infosec #cybersecurity #infoblox #malicious #parking #domains #clickfix #phishing #scam